Continuation of Solarwinds: The Story of Espionage and Exfiltration
Breaking It Down: How Did This Happen?
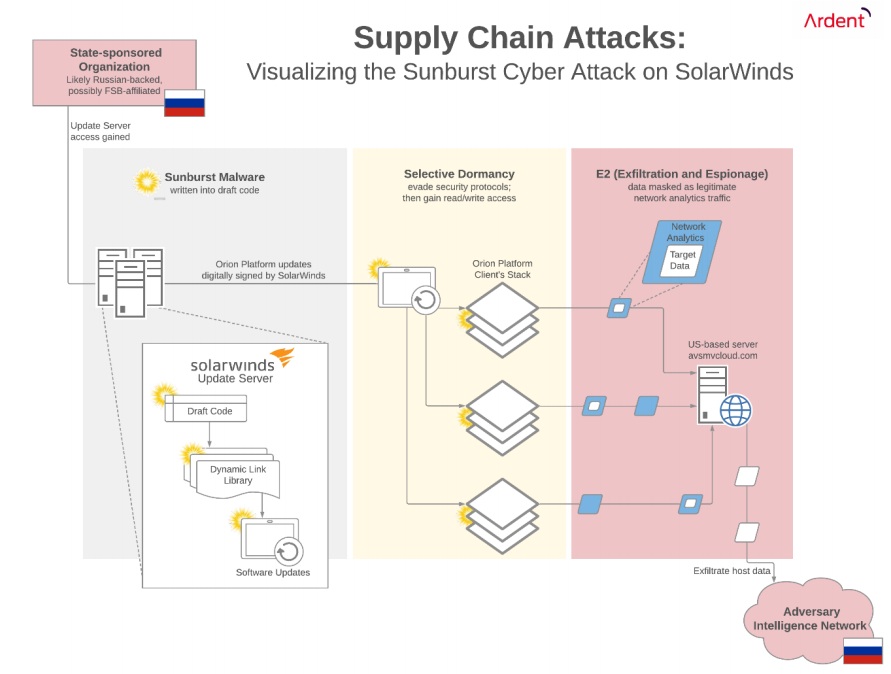
Sometime before March 2020, with evidence pointing to October 2019, hackers (likely state sponsored Russian agents) gained access to SolarWinds’s update server. In perhaps the most dramatic PSA for robust password management (or perhaps a shift towards passwordless security altogether), independent security researcher Vinoth Kumar found easy access to SolarWinds’s update server through the password “solarwinds123” (which was reported to the company in 2019).2 Cyber analysts are still unsure whether this specific vulnerability led to Russian access to the server. Regardless, this demonstrates that security was lacking as hackers found their way into a key system.
After gaining access to the update server, the hackers made small tweaks to the draft code used for periodic software updates. These tweaks to the draft code were written into DLL files (dynamic-link libraries) that were then compiled into final updates before being digitally signed by SolarWinds itself. These digital signatures masked the changes, making the files appear authentic to every system that reached out for an update. These tainted updates were eventually pushed out to over 18,000 SolarWinds’s clients.
The clandestine code effectively used the Orion Platform as the carrier to distribute itself, embedding access to core functions, and creating a backdoor into IT systems, including those at critical government agencies. The technique of using a less secure element of a system to gain access to a more secure element is a common tactic, an example of a Supply Chain Attack (SCA). Once delivered, the Sunburst malware acted as a Remote Access Trojan (RAT), enabling access to execute and transfer files, profile the system, reboot the machine, and disable system services.
Figure 2: Sunburst unknown unknowns
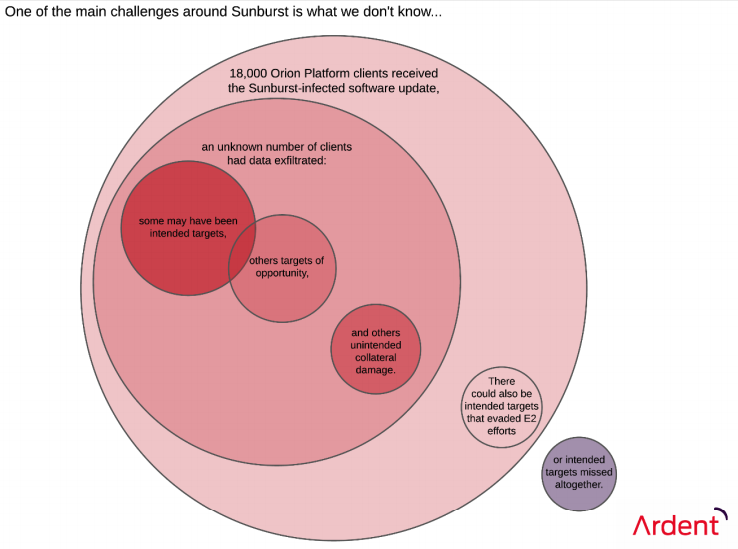
Why Didn’t They Catch It?
The real ingenuity behind Sunburst was that the malicious code maintained a very low profile on the system. Sophisticated in design, Sunburst intentionally minimized its footprint while testing and evading known security measures. After being embedded a client’s network, Sunburst would lay dormant for two weeks to avoid arousing suspicion or triggering an active security review.
“If Sunburst sensed any security threat to itself, it would go dormant again.”
After two weeks, Sunburst would activate and proceed through a detailed validation protocol using domain generation algorithms (DGAs) to test the DNS environment. It would check the domain name of the host system for key criteria, defensively evading anti-virus sandboxing, and security tools like Wireshark. Sunburst could choose to engage or not based on a variety of factors, including whether known security programs were active that could detect it. If Sunburst sensed any security threat to itself, it would go dormant again.
Only when it proceeded through its entire validation checklist would Sunburst begin its work and report back through data that mimicked legitimate network analytics traffic. To further obfuscate its activity, the hack’s data communications were being routed first to a US-based command and control (C&C) server using the domain avsmvcloud.com. This server was later used by FireEye (FEYE), Microsoft (MSFT), and GoDaddy (GDDY) as a kill switch to shut down the attack.
Figure 3: Sunburst distribution pathway
Sunbursts’ true danger to systems comes from the access that these techniques enabled over time. The breach was clandestine, likely sponsored by Russian state actors, and remained undetected for months. These factors created what the cybersecurity community calls an “Advanced Persistence Threat” (APT). A malicious user that is able to reconnoiter a network thoroughly can carry out more sophisticated and targeted espionage operations. APTs are focused on digital reconnaissance, gaining visibility of a network’s internal operating environment while remaining ready to exploit any vulnerabilities. Exploiting a network could mean orchestrating second-stage attacks or direct exfiltration of data.
As more information is released, the emerging consensus amongst both US intelligence agencies and private security professionals is that Sunburst was a Russian-engineered cyber 5 espionage attack. Moscow-based security firm Kaspersky Lab (whose itself is banned from use by US government agencies) noted that the malware behind Sunburst looked similar to a tool called Kazuar used by Turla, a hacking group that Estonian authorities believe operates on behalf of Russia’s Federal Security Service (FSB). Kaspersky detailed that similarities between the two include methods for obscuring functions, identification of victims, and the formula used to calculate the length of dormancy for the malware to avoid detection.
About Ardent Insights
Ardent Insights is a monthly blog series, showcasing ‘actionable intelligence’ on technology- and data-related risks and opportunities facing governments and the constituents they serve, especially in the realms of public safety, disaster management, national security, law enforcement, public health, and smart/resilient infrastructure and systems.
Continue reading the Solarwinds series to discover how this attack happened and what can be learned.